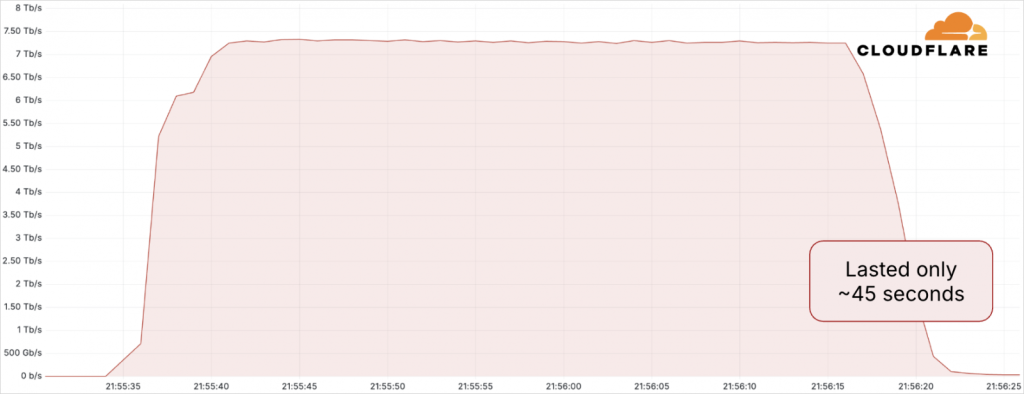
Cloudflare has done it again. In May 2025, the internet security company successfully blocked the largest-ever DDoS attack recorded to date. The attack peaked at a mind-blowing 7.3 Tbps and targeted a major hosting provider.
To put that in perspective, the attack pushed 37.4 terabytes of data in just 45 seconds. That is enough data to stream over 7,500 hours of HD video or view 12.5 million JPEG images, all in less than a minute.
What is a DDoS attack?
A Distributed Denial of Service (DDoS) attack is when attackers flood a server with so much traffic that it slows down or crashes. In this case, attackers used over 122,000 IP addresses from 161 countries, with major sources being Brazil, Vietnam, Taiwan, China, Indonesia, and Ukraine.
The goal? To overwhelm the system by bombarding it with junk traffic, what experts call “garbage” data packets. These packets hit over 34,000 ports per second at their peak, trying to sneak past firewalls and other defenses.
How Cloudflare Handled It
The victim was using Cloudflare’s Magic Transit, a service designed to stop DDoS attacks at the network level. Using its massive anycast network, Cloudflare redirected the attack across 477 data centers in 293 locations. Their system automatically analyzed the attack in real time and stopped itm without any human help.
This was made possible with advanced tools like:
- Real-time fingerprinting of traffic
- Gossiping between data centers to share intelligence instantly
- Automatic rule generation to stop attacks as they happen
The Attack Methods Used
While 99.996% of the traffic came from UDP floods, the attackers also used several techniques to try and stay undetected. These included:
- QOTD and Echo reflection
- NTP amplification
- Portmap and RIPv1 amplification
- The infamous Mirai botnet
These methods rely on outdated or misconfigured systems to boost the size of the attack. Even if they formed a small part of the traffic, they helped test the hosting provider’s defenses.
Cloudflare has added details from this attack to its DDoS Botnet Threat Feed, a free service that helps businesses block bad IPs in advance. Over 600 organizations already use it, and Cloudflare urges more to join.
Let me know if you want a LinkedIn post summary, a short tweet content, or a video script version of this article.




